This post was last updated on March 16th, 2017 at 07:27 am
Joomla, a free content management system (CMS), which is the 2nd most recognized and widely used CMS on the internet. It is 3.3% of all websites. It may not sound like a lot, but it is still millions of businesses and blogs that have chosen to run their websites with Joomla. Even though Joomla is a pretty secure CMS but as it's Open Source nature, Joomla always attracts a huge community of Hackers who constantly exploiting the software by finding vulnerabilities in the code of the Joomla application.
In this Joomla Security Checklist tutorial, I shared a list of best practices to harden your Joomla security and make your Joomla site an extremely tough nut to crack.
#1: Change the default administrator username and password to avoid brute-force attack
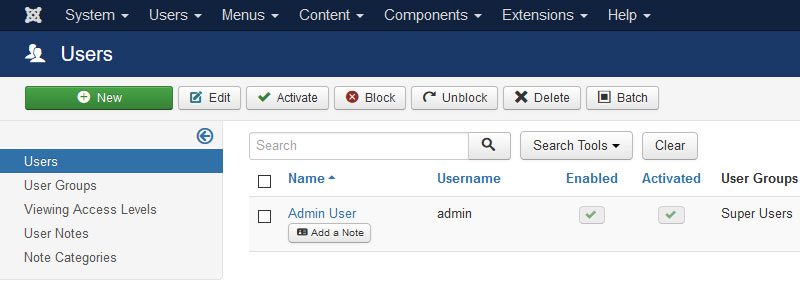
Don't leave default administrator account as "admin"; this is probably the biggest risk in Joomla. You must change default administrator login "admin" to something else.
Weak passwords are a common security hole, according to expert most of the attacks on websites because of weak passwords. Hackers use brute-force (using computer programs to guess password combinations in order to gain access to your control panel) technique to crack weak or easy passwords. Choose a password that other people won’t guess easily. The more complicated the password, more difficult it is for the attackers to crack it.
A strong password:
- Is at least 6-8 characters long
- Does not contain common words like pass, admin, admin123, etc
- Does not contain personal information like username, real name, or company name
- Is different from previously used passwords
- a combination of special characters ( *!@#)$ ), numbers and a mixture of uppercase, lowercase letters.
#2: Keep updated to the latest version of Joomla & Extensions
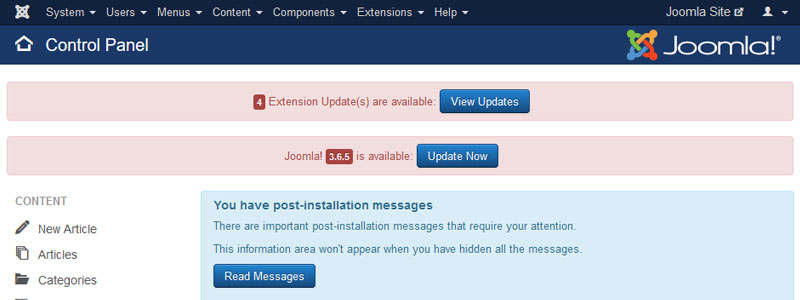
Most of the website owner don’t upgrade their CMS to the latest version. No matter what, always keep your Joomla up to date as well as all the extensions you're using. Always download extensions from trusted sites. Almost every release, you will notice some security fixes or a new addition to the system, which is for a reason and if you fall far behind you will be open to a lot of vulnerabilities, and hackers generally target older versions. Many vulnerabilities are resolved most of the times in later versions. Even if your Joomla doesn’t show if a new version is available regularly check on developer page.
Before installing any extensions, always backup your site's files and database. Install Akeeba Backup and configure it to backup regularly to an off-site location.
#3: Delete files in the "tmp" folder and maintain it clean
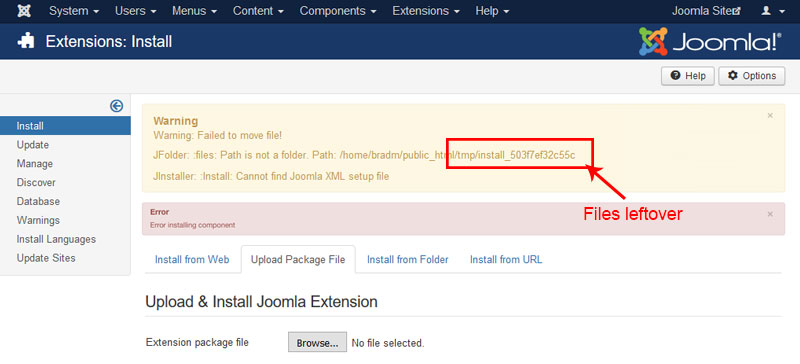
The "tmp (temporary)" folder is used by Joomla and its extensions to store files on a temporary basis. During an extension installation process, a copy of the extension's archive file is copied into the "tmp" folder to unpack into the correct folders.
Most of the time the install process cleans the "tmp" folder automatically. But sometimes it will collect copies of archive files or due to a failed installations process, files get stuck in the "tmp" folder. Since these files may come from old extensions once installed on your website, can contain old vulnerable and insecure code.
So the best practice is to delete such files and keep your website clean, something that you should periodically perform. You can also automate the process of auto-cleaning the "tmp" folder by using NoNumber's Cache Cleaner, a free plugin which provides a setting for emptying the "tmp" folder.
You should only keep the index.html file in place, that may prevent potential directory listing of the files.
#4: Check your extensions for known vulnerabilities
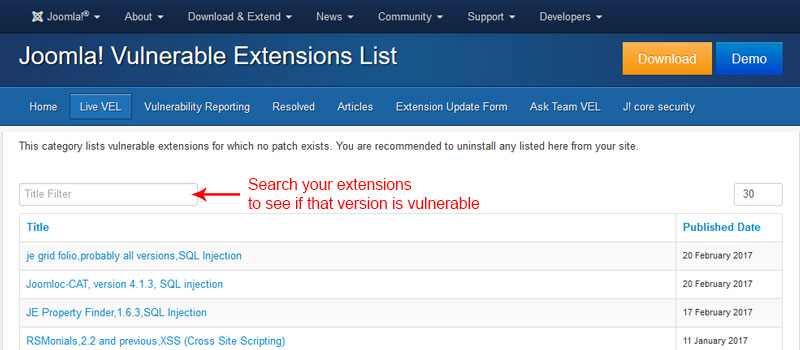
Most security vulnerabilities on Joomla site are caused by 3rd party extensions. Before installing any extensions, check the Official List of Vulnerable Extensions. There's an entire forum dedicated to vulnerable third part extensions. Subscribe to it. Joomla Core Security Notifications system notifies its members when a vulnerability is discovered in the Joomla core or when an extension has been discovered to have a vulnerability.
Even if there are no known vulnerabilities for the installed extensions now, that doesn't mean that one won't be vulnerable in the future. It's a best practice to uninstall non-core unused extensions that aren't being used.
#5: Use appropriate file permissions & ownership
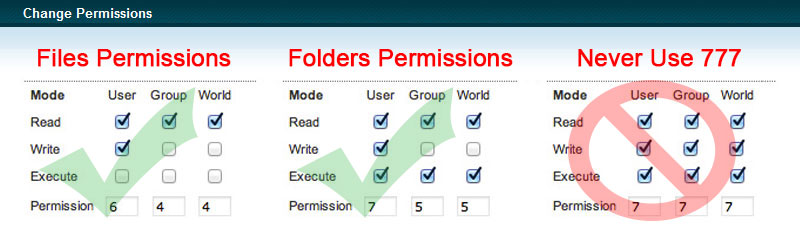
File permissions determine what you and other people can do with a file or folder. Setting the right permissions is must to secured your Joomla website. If your permissions are too loose this could open up a door for an intruder and if they are too restrictive this could break your Joomla install. Take extra care because Joomla installation needs to be able to write to certain directories.
Usually, Joomla recommends the following configuration on default installs:
- All files should be set with a CHMOD value of 644
- All folders should be set with a CHMOD value of 755
- Your configuration.php file should be set with a CHMOD value of 640
Joomla has good documentation on security permissions.
#6: Use Joomla security extensions

Whether you have a huge website or a small homepage you need to take care of your website's security because it will always be a target for hackers. Using security extensions not only prevent different types of attacks but also improve your Joomla website protections by scanning files and folders of your website even if it's not a part of Joomla core files.
Below you will find some of the most popular(with good reviews) Joomla security extensions:
#7: Enable search engine friendly (SEF) URLs
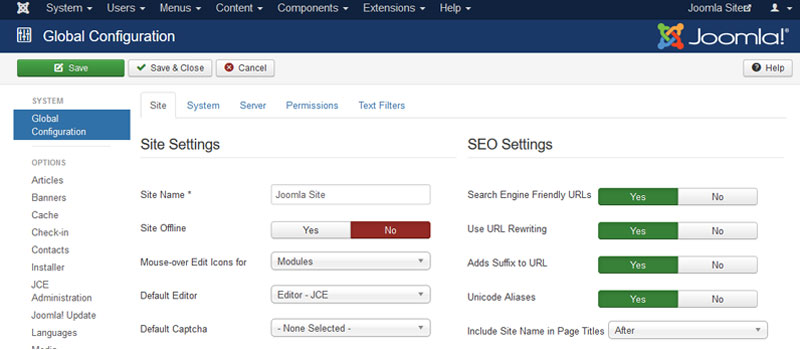
It is always advised to enable search engine friendly URLS and hide the file names such as index.php from appearing in your URL structure. This helps mask information and prevent hackers from finding vulnerabilities.
Note: You must Rename htaccess.txt to .htaccess before enable.
#8: Disabled error reporting
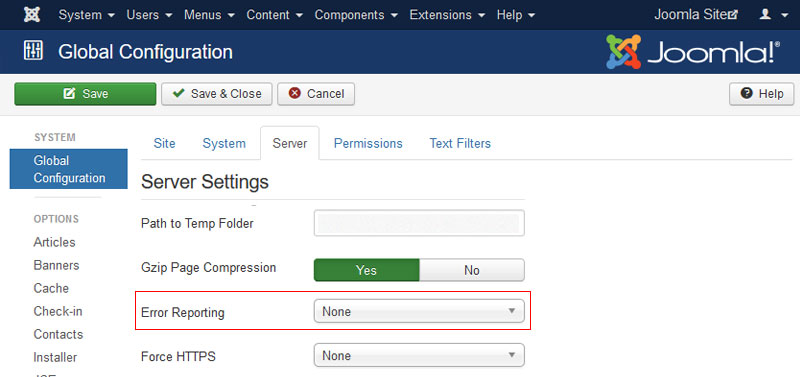
Make sure that error reporting is set to none for your live site. This is simply to avoid information disclosure. Hackers may attempt to disrupt the operation of your site in order to gain information like, the file paths being used. By disabling error reporting, we can make sure, we provide no information about most errors they can generate.
#9: Additional rewrite rules to Joomla .htaccess
You can enhance both the security and the speed performance of your website through htaccess, but it's not the only thing you need to do.
Paste this code just after 'RewriteEngine On'
########## Begin - Rewrite rules to block out some common exploits
## If you experience problems on your site block out the operations listed below
## This attempts to block the most common type of exploit `attempts` to Joomla!
#
# Block out any script trying to set a mosConfig value through the URL
RewriteCond %{QUERY_STRING} mosConfig_[a-zA-Z_]{1,21}(=|%3D) [OR]
# Block out any script trying to base64_encode crap to send via URL
RewriteCond %{QUERY_STRING} base64_encode.*(.*) [OR]
# Block out any script that includes a tag in URL
RewriteCond %{QUERY_STRING} (|%3E) [NC,OR]
# Block out any script trying to set a PHP GLOBALS variable via URL
RewriteCond %{QUERY_STRING} GLOBALS(=|[|%[0-9A-Z]{0,2}) [OR]
# Block out any script trying to modify a _REQUEST variable via URL
RewriteCond %{QUERY_STRING} _REQUEST(=|[|%[0-9A-Z]{0,2})
# Send all blocked request to homepage with 403 Forbidden error!
RewriteRule ^(.*)$ index.php [F,L]
#
########## End - Rewrite rules to block out some common exploits
########## Start- Rewrite rules to block all attempts to run scripts outside the Joomla control.
RewriteCond %{REQUEST_URI} ^/images/ [NC,OR]
RewriteCond %{REQUEST_URI} ^/media/ [NC,OR]
RewriteCond %{REQUEST_URI} ^/logs/ [NC,OR]
RewriteCond %{REQUEST_URI} ^/tmp/
RewriteRule .*.(phps?|sh|pl|cgi|py)$ - [F]
########## End - Rewrite rules to block all attempts to run scripts outside the Joomla control.Finally, you can find there are many ways you can harden your Joomla website security and some great extensions to help you do so. It may take a bit of work to go through these, but if you ever visited the Joomla security forums, you'll find stories about people wasting huge amounts of time dealing with a hacked websites. The last thing is always backup of your live website. It's not just hacking that may compromise your website but other factors like a faulty upgrade or extension install.
I hope you found this Joomla security checklist helpful, be kind to help others by sharing it to Facebook, Twitter, or LinkedIn using the buttons below.


Leave A Reply